
Information about security and authentication
Background analysis
With the development of Internet technology, network security has become more and more popular in daily life, and network security has gradually become the focus of wide attention of people. The security demands that follow have been put on the agenda.
Six ways to leak Information

Four major problems of password security
- 1.Tedious multi-platform authentication
- QQ, alipay and bank accounts are logged into accounts on multiple platforms, making it difficult to remember or reuse passwords, making the password security coefficient of accounts low and the risk of forgetting and stealing more and more high.
- 2. Weak password
- For the convenience of using passwords, users often use their own birthday, phone Numbers, words and so on as passwords, these weak passwords are very easy to crack.
- 3. Hacking
- More and more developed network information, personal information will be leaked even if it is careless, hackers, trojans, phishing websites emerge in endlessly, and even information theft by competitors.
- 4. Company management
- When employees enter and leave the company, their rights are transferred.
Solution
In the face of many personal and corporate privacy and property security problems, shenzhen haiyue communication technology co., LTD. Has developed a dynamic password authentication solution.
Knowledge of dynamic cryptography
Noun explanation
-

Static password
The static password involved in this document is the fixed password normally set for the user.
-

Dynamic password
Seamoon's dynamic password authentication solution is a one-time password generated by OATH algorithm and a time-varying dynamic password based on SMS, APP and hardware token.
-

OATH algorithm
OATH algorithm is a recognized security algorithm in the international OTP field. If the OATH algorithm runs for a single time <1ms,it takes a very short time and consumes very little power. The OATH algorithm is used in this solution.
Dynamic cryptographic medium
The dynamic password solutions of Seamoon are all in the form of hardware token and APP.
-
SMS
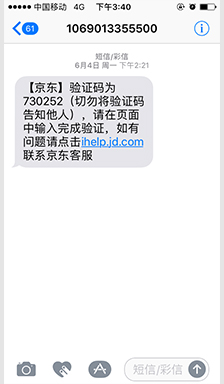
-
APP
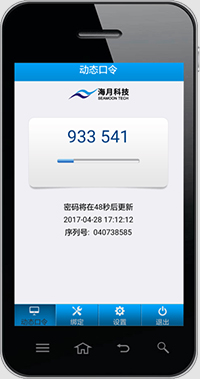
-
Hardware token

Dynamic password type
-

Usage: when using Seamoon dynamic password card, the password card generates a different, one-time password every 60 seconds.
-

Usage: when using Seamoon dynamic password card, the key automatically triggers a new one-time password.
-

Usage: when using Seamoon dynamic password card, the user triggers a new one-time password according to the login prompt message.
Dynamic password token usage
-
Time
Time-based dynamic password authentication solutions are divided into long-display time tokens, key-based time tokens and APP-based time-based dynamic tokens.
Long-display
Long-time dynamic password token is the client device, the server time synchronization mechanism is used to produce the disposable dynamic password, convenient operation, the user login system when required to enter the dynamic password, simply enter the token display on dynamic password to complete the login (dynamic password every 20s/30s to 60s at a time of change).
Key-based
Key-based password token server time synchronization mechanism is used to produce disposable dynamic password OTP, when required to enter the dynamic password user login system, as long as the press of a button on the token, will be randomly generated a serial port to every 20s/30s to 60s is changed), customer input dynamic password to complete the login.
-
Event
Event-type token use the mechanism of server and token key number event calculation synchronization to produce one-time dynamic password OTP, and adopts the mechanism of synchronous event to generate dynamic password.
-
Challenge response type
Challenge response type dynamic token use the challenge response and one-time password algorithm is a combination of dynamic password authentication token integration and function of online trading signature, in the process of the realization of the input data, all data input operation through data input device input directly to the electronic signature work, be safe, reliable, and easy to use, easy to operate. The token has the function of starting PIN code protection to protect the user token from being misappropriated, misused and identity fraud. The challenge response token can provide a fully functional, highly secure authentication solution for customers.

